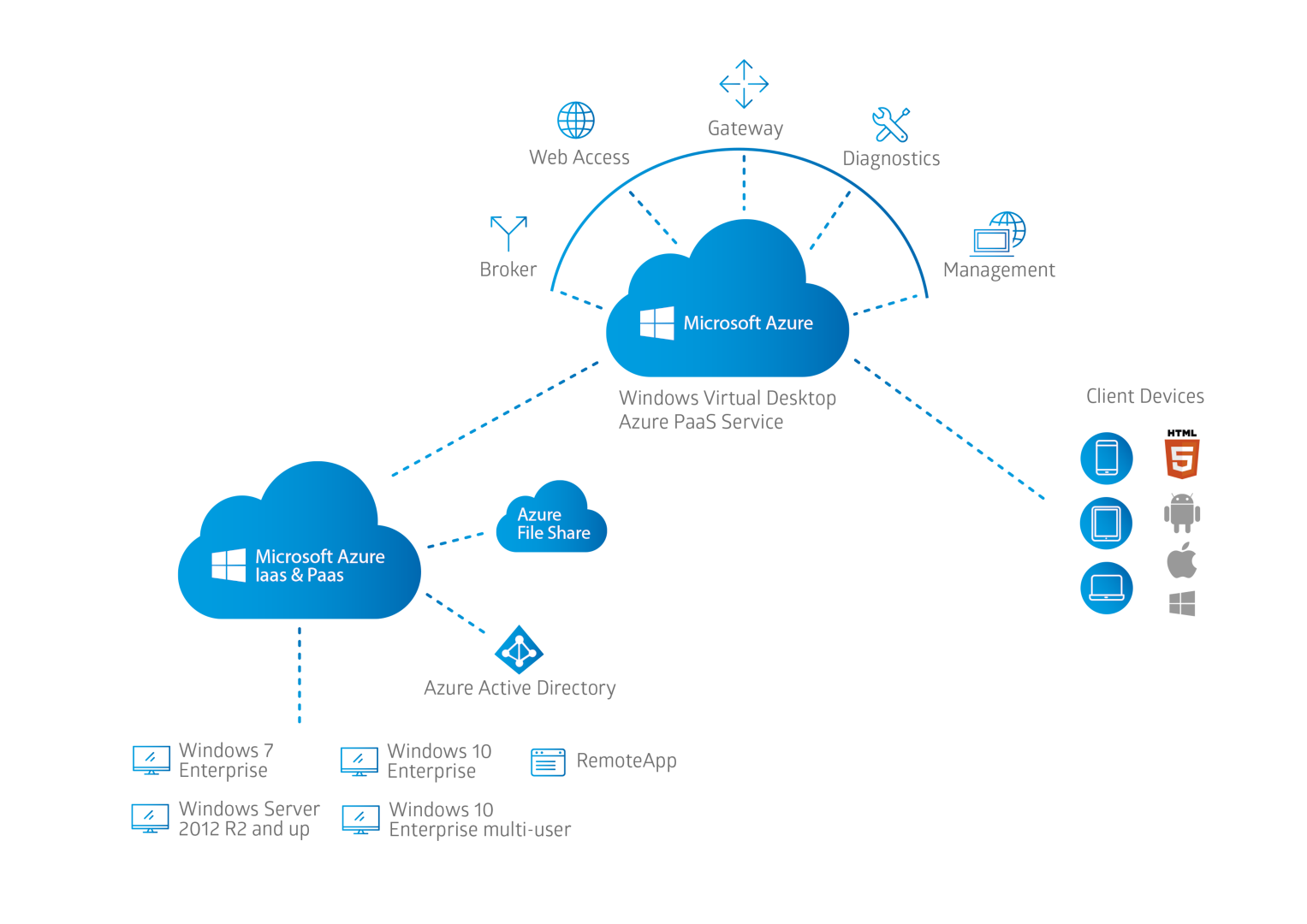
Awesome news today: Windows Virtual Desktop is now General Available!

Cloud.Architect Blog

Awesome news today: Windows Virtual Desktop is now General Available!
Simply said: it has been really crazy the last 2 years…
If you are using ARM-templates & Desired State Configuration (DSC) for your RDS deployments, you will be able to cover almost all your needs. But you could also use different options or technologies for your needs.